How to break MAC filtering (wifi security)
How to break MAC filtering (wifi security)
How to break MAC filtering was probably the first question that followed the invention of the MAC filtering concept and was asked in the same minute when MAC filtering was introduced as a security concept.
Many people still use MAC filtering or MAC addressing as a security measure for their wireless networks, but the sad truth is that MAC filtering is very easy to break; it might even be the easiest security measure to break. Luckily, the population of such wireless users has been rapidly decreasing. This page describes the concept of MAC filtering and demonstrates how easily broken it can be.
What is MAC filtering?
First, let's make clear what we are talking about. When you set up your wireless network, you usually operate in so-called infrastructure mode. Infrastructure mode means that you have some wireless access point sitting somewhere in your room or office, and you connect your laptops and other wireless devices to it as you please, and as you move around the building.
To introduce some security into the system, you allow only certain MAC addresses to connect to your wireless access point. This is set up in your wireless router administration interface. Laptops and devices with MAC addresses not included by you or your wireless admin in your wireless access point MAC access table are not allowed to use your network. In other words, MAC filtering is used to restrict network access to authorized devices. Sounds secure? You can read more about this in our Wireless Wi-Fi network security tutorial 101 (part 1).
Why is MAC filtering so easy to break?
MAC filtering is very easy to break for one major reason. If you look at the network traffic (use for example tcpdump or ngrep in Linux), you can see that MAC addresses do not get encrypted when traveling over the air between your laptop and your wireless access point.
There are many tools on the internet which can sniff the network traffic and show you all the information that you need. Windows users know for example NetStumbler, Linux users find airodump-ng useful.
The following print screen shows what anyone can easily find out about your network using for example the airodump-ng Linux utility:sudo airodump-ng -c 11 --bssid 00:1A:92:77:BB:D9 -w kerim wifi0
where -c is the channel on which to listen to network traffic, --bssid is the MAC address of the wireless access point (obtained from the same utility but different options), -w is the name of file to which the network communication should be dumped, wifi0 is the name of the network adapter.
The print screen below shows the MAC address of a wireless access point (BSSID), the name of the wireless network (ESSID), channel on which the wireless network operates (CH), what type of encryption is used if any (ENC, CIPHER), the strength of the signal (PWR), and of course MAC addresses of devices currently connected to the network (STATION).
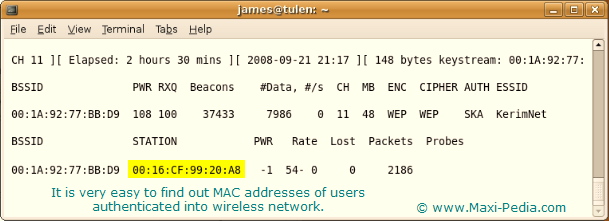
Once you have the MAC addresses of connected devices, you can mask your self to behave as one of them. Getting other's MAC addresses is also called MAC spoofing.
How can anyone get my MAC address when it is encrypted?
That is the misconception. Even if you employ WEP, WPA, WPA-PSK and other encryption in your network, it does not mean that your MAC and IP address is encrypted, and it still can be easily obtained from network traffic. The following page demonstrates how you can listen to network traffic: How to find MAC and IP addresses in network data stream.
But isn't my MAC address unique?
Yes, it is. Every networking device has a unique identifier that is burned into the hardware by the manufacturer. In case of network cards, it is the MAC address that we are talking about. You cannot change the MAC address that is burned into your network card, but you can tell your operating system to change information about your MAC address in every data packet it sends out to the network. So, in effect, MAC spoofing is sort of a MAC faking. You make everyone out there believe that the MAC address that you broadcast in your data packets is the one you really have in your network interface.
Won't data packets with the same MAC address collide?
Yes, they will, but it is not a problem that would cause the end of the world. Remember that once you authenticate and associate into a network, you get your own IP address from the wireless router (assuming DHCP is enabled), and all network communication goes by your IP address. Before you authenticate into the network, packets with the same MAC address can collide, but network devices have mechanisms built into them to deal with "bad" data. If for example two exactly the same data packets were sent from two laptops to wireless router at exactly the same time, the router would just discard them and wait for next transmission which would most likely not be identical.
How can I change my MAC address?
As with anything, you can find many utilities for this purpose on the web. Windows users know for example Macshift. Linux users can use the Macchanger command. The following print screen shows how to change a MAC address in Linux. You can find a print screens for both Windows and Linux on the Macshift and Macchanger pages.
Change MAC address in Linux (Ubuntu)
Let's take a look at the details. If you go with the Macchanger utility in Linux (Ubuntu), you can use it as follows in your terminal window:
sudo macchanger -m 12:34:56:12:34:56 [adapter name]
Sudo tells the computer that you are executing the command as the administrator. Macchanger is the utility to change your MAC address. Option -m is to be used together with the MAC address parameter followed by the name of the network interface for which you wish to change the MAC address. The name of the wireless interface (rausb0, wlan0, wifi0, etc.) can be found by typing iwconfig.
If you get the Can't change MAC: interface up or not permission: Device or resource busy message when executing macchanger, you need to disable the device first. That can be done by typing the sudo ifconfig [adapter name] down command, where the [adapter name] is the name of your network interface again. Do not forget to enable the interface back after changing the MAC address. You can verify your new MAC by typing sudo ifconfig [adapter name]. More details about this are available on the Macchanger page. You can also see more details in the next print screen:
Now you are free to authenticate and associate into your desired network.
Change MAC address in Windows
Changing your MAC address in Windows is even easier. You can use for example the Macshift utility.
More details about this are available on the Macshift page. You can also see more details in the next print screen:
Very easy, isn't it?
Is MAC spoofing OK?
Is changing your MAC address and connecting to your neighbor's network ok? As long as the neighbor knows about it, then it is ok. Connecting to someone's network without the owner's knowledge with the intention of gaining some benefits is not ok. It is also needed to say that only a very small percentage of people use MAC filtering as the only security measure today, and educational efforts such as this page and your testing and desire for learning are one of the ways to promote improvements and to convince others to implement more secure measures. If you break someone's MAC filtering, make sure they know about it and take it as their good neighbor's advice - after breaking someone MAC filtering, help them and advice them on how to be more secure. How? See here: about WPA, WPA2, PSK, IPSec, VPN, and WiFi security tips.
Interested in more fun stuff? Check out our other articles:
How to crack WEP encryption
How to crack WEP with Intel PRO/Wireless 3945ABG
In casef you have questions about MAC spoofing, you are welcome to visit our IT discussion forum and submit your questions there.
It is easy, just include the code provided below into your HTML code.
 Delicious
Delicious Digg
Digg StumbleUpon
StumbleUpon Furl
Furl Facebook
Facebook Google
Google Yahoo
Yahoo