How to find MAC and IP addresses in network data
How to find MAC and IP addresses in network data
How easy is it to obtain MAC address and IP address from wireless network traffic? We have asked this question and now provide this writeup to demonstrate how vulnerable MAC addressing is as a security measure. Even though the number of users protecting their wireless networks with the MAC filtering technique as the only measure is decreasing, there are still many of them.
MAC addressing?
This page relates to the security concept called MAC addressing or MAC filtering which we described in more details on the following page: Wireless security: MAC addressing. The Wireless security: MAC addressing article describes what MAC addressing is and how it works.
We took our explanation to the next level by providing also one other analysis in which we attempted to break MAC filtering. We write about this on the How to break MAC filtering (wifi security) page. On this page, we used some utilities that provided us with the MAC address of an already authenticated client (i.e. someone that is already using the wireless network that we are trying to break into). But, some inquisitive people may ask:
"How do those utilities get the MAC address?" or
"How can I get a MAC address or an IP address from simple listening to network traffic?"
On both pages referenced above, the Wireless security: MAC addressing and How to break MAC filtering, we claimed that information about MAC addresses and IP addresses is not encrypted when the wireless access point sends data to connected devices and receives it back. Information not being encrypted is the key knowledge here, and this is true even with WEP and WPA encryption standards. Let's prove it!
Unencrypted information sent over encrypted protocols?
Everyone talks about WEP, WPA, WPA2, WPA-PSK, and others so you might be misled and thinking that if your network is WEP or WPA protected, all your data is encrypted. Only half of this is truth. When data is transmitted over the network, it is organized in so-called packets or datagrams. Every network packet includes two parts:
a) header
b) data
The data section of a packet can be encrypted with WEP, WPA, or some other mechanism. This is the part that contains your data and is safe. But, packet headers are not encrypted in most cases. Depending on the protocol and packet type, packet headers include information about the type of protocol that is used to transmit the data, length of packet, flags, and among others also IP addresses and MAC addresses. We can get information about IP addresses and MAC addresses by simply listening to network traffic and analyzing its content. It is easier than it might seem.
How can I discover a MAC address from network traffic?
As with anything in the IT industry, there are many ways to sniff network traffic and analyze its content. We have chosen Linux (UBUNTU) platform and the tcpdump utility. We listened network traffic on the TCP/IP protocol.
MAC addresses are not included in all network packets. In order to obtain a MAC address, you have to listen to specific type of network traffic, for example the ARP messages. First, let's explain what ARP is and how it works.Every device on the internet is identified by two addresses - IP address and MAC address. IP address is what the Internet understands, MAC address is what a computer needs to communicate with other computers on the Ethernet level. To make the story short, Address Resolution Protocol (ARP) is used to locate the MAC address associated with a desired IP address. ARP exists solely to glue together the IP and Ethernet networking layers. Let's demonstrate this using an example:
Assume we have two computers, computer A has IP address 192.168.1.1 and the other computer B has IP address 192.168.1.104. Now, the B computer wants to send a message to the computer A, but it does not know the MAC address of computer A, so it sends out an ARP request to discover the MAC address. It is a broadcast message which every device on the network can hear. The message is something like:
"Hey, I am 192.168.1.104, can anyone tell me who has 192.168.1.1?"
If a host A with IPv4 address of 192.168.1.104 is running and available, then it would receive the ARP request and send a reply packet back to B providing its MAC address in the sender hardware address field. It would be a unicast message saying something like:
"Hey, I am 192.168.1.1 and my MAC address is 00:19:e0:a0:9a:70. I am listening to you."
Now that computer B has the target computer MAC address, it can send its message to just this one guy. In other words, once the requestor receives the response packet, it associates the MAC address and the IP address.
And why do we need two addresses after all? Since networking hardware such as switches, hubs, and bridges operate on Ethernet frames, they are unaware of the higher layer data carried by these frames. Similarly, IP layer devices, operating on IP packets need to be able to transmit their IP data on Ethernets. ARP defines the conversation by which IP capable hosts can exchange mappings of their Ethernet and IP addressing.
If we can listen to ARP packets, we can get the MAC address information. We can listen to network traffic using for example the tcpdump Linux command line utility.
sudo tcpdump -ennqti wlan0 \( arp or icmp \) -xX
This command results in the following outcome:
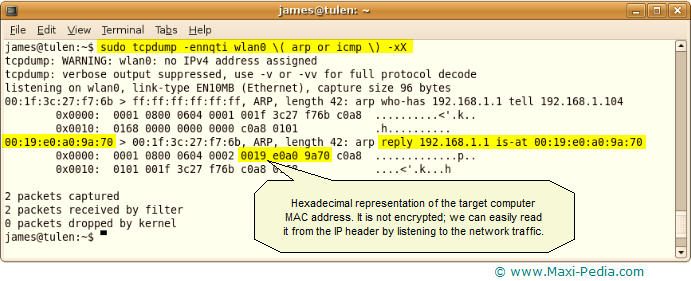
This example is the commonest example of ARP traffic on an Ethernet. The line which starts 00:19:e0... is the reply from the computer A to the computer B. The row of numbers is a hexadecimal representation of the network data. Each 2 numbers is one byte, so for example 0001 is two bytes. IP headers have a pre-defined structure and we know that our type of header provides information about the sender's MAC address starting the 9th byte. MAC address is 6 bytes long, so we know the MAC address of computer A must be 00:19:e0:a0:9a:70.
How can I find an IP address in network traffic?
This is even easier than finding a MAC address. Finding an IP address can be done in many ways; we will focus on how to obtain IP address by listening to network traffic and analyzing data packets.
We will use Linux (UBUNTU) and the tcpdump utility again. Finding IP address is easier than finding MAC address because it is included in the header of every network packet. You can listen to network communication by executing the following command:
sudo tcpdump -qec1 -i wlan0 -x
This command will produce the following:
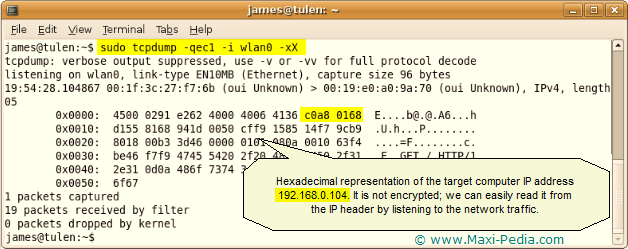
Obtaining an IP address was a one-line task. The hexadecimal c0a8 0168 translates to 192.168.1.104. This is how it is calculated:
c0 = (12 x 16) + (0 x 1) = 192
a8 = (10 x 16) + (8 x 1) = 168
01 = ( 0 x 16) + (1 x 1) = 1
68 = ( 6 x 16) + (8 x 1) = 104
More importantly, we have demonstrated that IP address information is not encrypted when traveling over the network and can be easily spoofed. You can read more on TCP/IP at these two websites: http://tutorials.papamike.ca/pub/tcpdump.html and http://homepages.uel.ac.uk/u0110214/PacketStruckture.htm.
It does not work!
Does not work for you? Feel free to ask a question in our discussion forum. By the way, you might be interested in the following article: How to crack WEP. Or, some of the resources below might help too.
It is easy, just include the code provided below into your HTML code.
 Delicious
Delicious Digg
Digg StumbleUpon
StumbleUpon Furl
Furl Facebook
Facebook Google
Google Yahoo
Yahoo